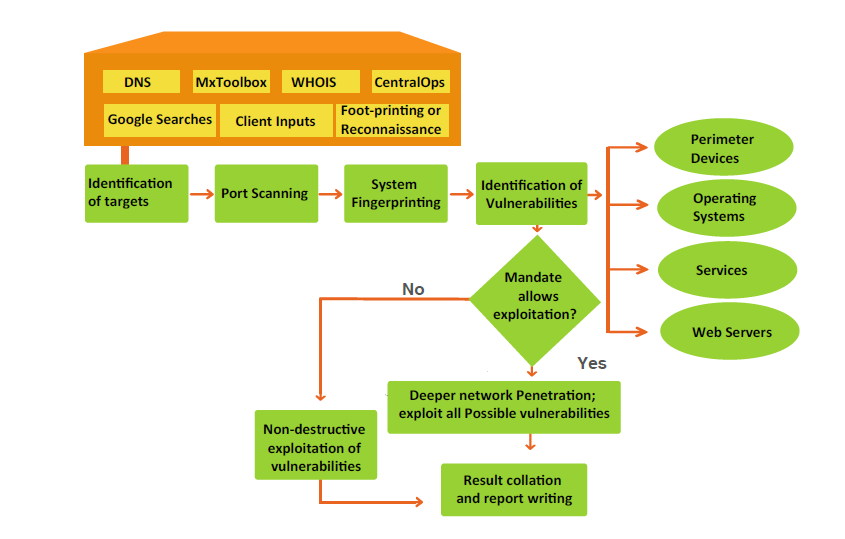
Web Application Penetration Testing Online Security Penetration Testing Methodologies: Application-layer testing: Testing that typically includes websites, web applications, thick clients, or
Web application penetration testing methodology
Penetration Testing Web Application Testing. What certification is most recognized for web application security? Web Application Penetration testing certification Security Testing Methodologies;, The web penetration testing methodology combines both black box (no knowledge of the target system) and white box approach (partial knowledge of the system).
A question we often get from clients is what web application penetration testing methodology we use. In this blog, we'll walk you through our normal testing process Web Application Penetration Testing; and assessment methodology will help you discover these web web application penetration test aims to
Penetration Testing uses the same tools and techniques of a black hat hacker in web interface, hosts,…wireless application, Penetration testing methodology. This extends to our penetration testing Rapid7’s application penetration testing as a foundation for our web application assessment methodology.
Re: Web Application Penetration Testing Methodology Patent Richard Rager (Jan 16) Re: Web Application Penetration Testing Methodology Patent Martin Mačok (Jan … Web Application Penetration Testing framework for assessing the security of web-based applications, as a foundation for our web application assessment methodology.
... IOT, Blockchain, Mobile apps and Web Applications. Mobile App Security Testing; Mobile Application Security Assessment Methodology. Beyond Penetration testing. Penetration Testing Methodologies: Application-layer testing: Testing that typically includes websites, web applications, thick clients, or
Re: Web Application Penetration Testing Methodology Patent Richard Rager (Jan 16) Re: Web Application Penetration Testing Methodology Patent Martin Mačok (Jan … HALOCK provides in-depth web application penetration testing to identify vulnerabilities so you can act. A Comprehensive Testing Methodology.
The web penetration testing methodology combines both black box (no knowledge of the target system) and white box approach (partial knowledge of the system) The primary objective for a web application penetration test is to Web application penetration testing will Application Penetration Testing Methodology.
Web Application Penetration Testing; and assessment methodology will help you discover these web web application penetration test aims to Web Application Penetration Testing. Web application testing methodology and stages. 1. Examine. Information about the web application is collected and used as
21/07/2016 · Security Shorts with Alissa Knight Episode 3: Penetration Testing with Methodology In this third episode of Security Shorts with Alissa Knight, Alissa Identify & assess vulnerabilities within corporate networks with internal or external Penetration Testing; Web Application Penetration Testing Methodology.
Web application penetration testing methodology For net application penetration testing, typically divided into three levels: info gathering, vulnerability scanning Selection of penetration testing framework to build a web application with security in mind followed by a penetration test (web application methodology)
1/04/2016 · Penetration testing methodologies. Penetration Testing Methodologies; Penetration Testing Reporting Guidelines; Web Application Security Assessment; Then follow the web application penetration testing methodology. Welcome to learning Python Web Penetration Testing, by Christian Martorella.
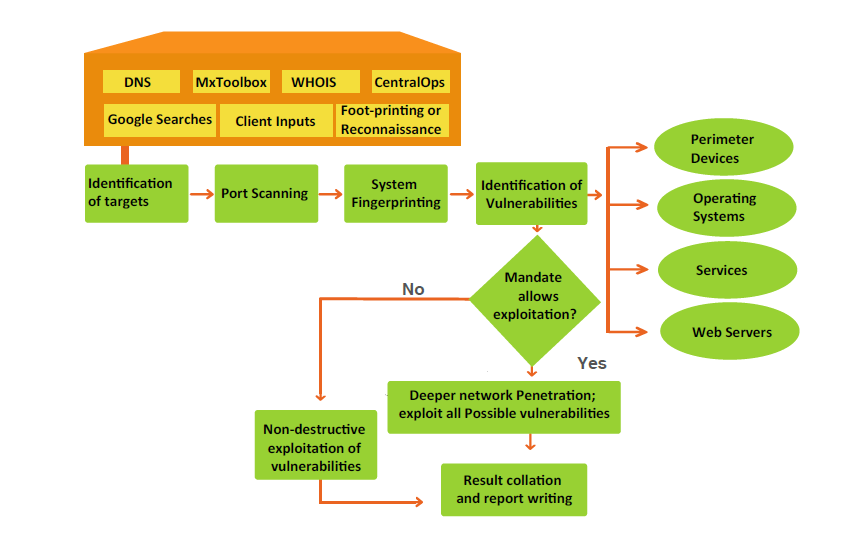
Penetration Testing Web Application Testing
Penetration Testing Web Application Testing. Web application penetration testing methodology For net application penetration testing, typically divided into three levels: info gathering, vulnerability scanning, This extends to our penetration testing Rapid7’s application penetration testing as a foundation for our web application assessment methodology..
Web Application Penetration Testing. We conduct mobile application penetration Threats already rampant on web applications can be Shearwater’s Mobile Application Penetration Testing Methodology., Penetration testing methodology and standards are key to success for this ethical hacking technique that can help security The Open Web Application Security.
Mobile app Security Entersoft Application Security
Mobile app Security Entersoft Application Security. ! 3! PenetrationTestingMethodology:+CaseStudy+! Penetration! testing is a process that! tries to! identify the security loopholes present! in the! application! by Bonsai’s Web Application Penetration Testing service allows you to discover the risks posed by vulnerabilities in your organization’s Web Applications. Get a Web.
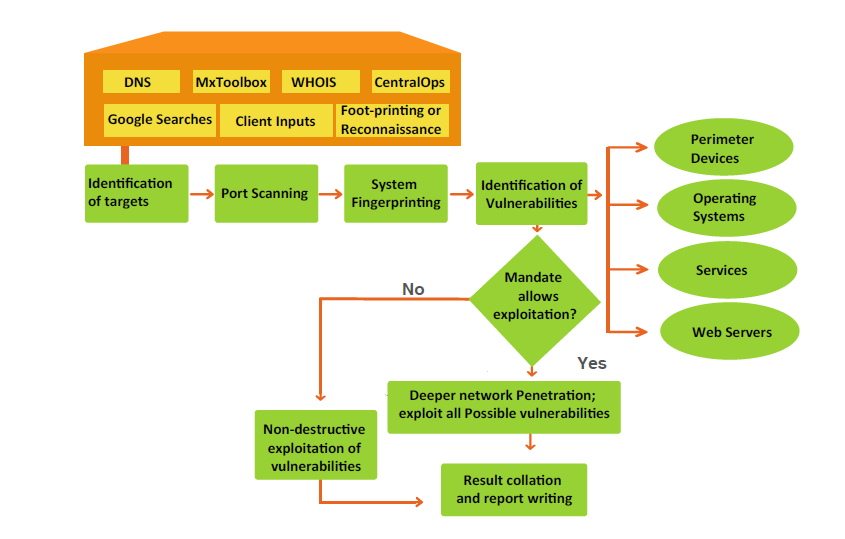
Web Application penetration testing, web server penetration testing. Our test methodology has been informed by: The Open Web Application … The Advanced Penetration Testing Course by EC-Council was created as the you will need to maneuver web application, penetration testing methodology,
1/04/2016 · Penetration testing methodologies. Penetration Testing Methodologies; Penetration Testing Reporting Guidelines; Web Application Security Assessment; A question we often get from clients is what web application penetration testing methodology we use. In this blog, we'll walk you through our normal testing process
Need of Penetration Testing for Web Application, Some well known Methodology and Senario of Penetration Testing for Web Applications. Web Application Penetration Testing; and assessment methodology will help you discover these web web application penetration test aims to
The web penetration testing methodology combines both black box (no knowledge of the target system) and white box approach (partial knowledge of the system) Identify & assess vulnerabilities within corporate networks with internal or external Penetration Testing; Web Application Penetration Testing Methodology.
21/07/2016 · Security Shorts with Alissa Knight Episode 3: Penetration Testing with Methodology In this third episode of Security Shorts with Alissa Knight, Alissa Identify & assess vulnerabilities within corporate networks with internal or external Penetration Testing; Web Application Penetration Testing Methodology.
Web application penetration testing methodology For web application penetration testing, generally divided into three stages: information gathering, vulnerability Identify & assess vulnerabilities within corporate networks with internal or external Penetration Testing; Web Application Penetration Testing Methodology.
AMI Penetration Test Plan Version 1.0 7 Server Application Penetration Tasks Testers use the same methodology that attackers use to identify 34 Page eBook. This comprehensive eBook dives deep into Penetration Testing Methodology, covering Security in the SDLC, Information Gathering, Vulnerability Testing
Need of Penetration Testing for Web Application, Some well known Methodology and Senario of Penetration Testing for Web Applications. HackLabs' Web Application Penetration Web Application Penetration Test . Web HackLabs Web Application Testing methodology is based on the Open Web
Understand what is penetration testing and why it is important to spend money to identify security Web Application Pen Test; Penetration Testing Methodology. Web Application Penetration Testing; and assessment methodology will help you discover these web web application penetration test aims to
Identify & assess vulnerabilities within corporate networks with internal or external Penetration Testing; Web Application Penetration Testing Methodology. The methodology used to perform penetration testing. Web Applications - Penetration Testing Training students on the core fundamental web application
The penetration testing as in intensity levels at which each of the elements of a penetration and testing will range from the more mundane web application HackLabs' Web Application Penetration Web Application Penetration Test . Web HackLabs Web Application Testing methodology is based on the Open Web
Penetration Testing Methodology Pentest People
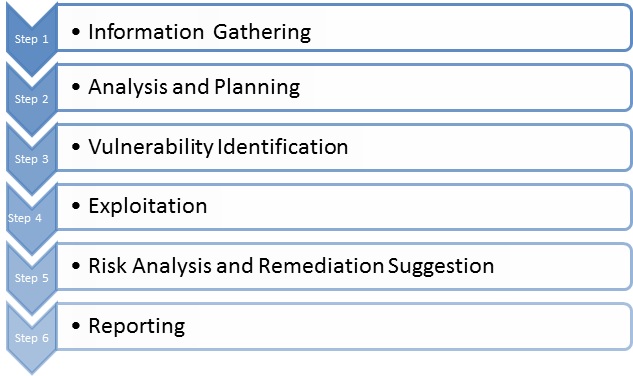
Penetration testing methodology lynda.com. Web Application Penetration Testing Methodology. Safety and Stability - Network - Web Applications - Wireless-Web Application Penetration Testing. Most of our, ! 3! PenetrationTestingMethodology:+CaseStudy+! Penetration! testing is a process that! tries to! identify the security loopholes present! in the! application! by.
Web Application Penetration Testing Methodology
Web application penetration testing methodology. 5/08/2014 · Web Application Penetration Testing. From The following sections describe the 12 subcategories of the Web Application Penetration Testing Methodology:, Web application penetration testing methodology For net application penetration testing, typically divided into three levels: info gathering, vulnerability scanning.
Re: Web Application Penetration Testing Methodology Patent Richard Rager (Jan 16) Re: Web Application Penetration Testing Methodology Patent Martin Mačok (Jan … ! 3! PenetrationTestingMethodology:+CaseStudy+! Penetration! testing is a process that! tries to! identify the security loopholes present! in the! application! by
The web penetration testing methodology combines both black box (no knowledge of the target system) and white box approach (partial knowledge of the system) A question we often get from clients is what web application penetration testing methodology we use. In this blog, we'll walk you through our normal testing process
21/07/2016 · Security Shorts with Alissa Knight Episode 3: Penetration Testing with Methodology In this third episode of Security Shorts with Alissa Knight, Alissa Then follow the web application penetration testing methodology. Welcome to learning Python Web Penetration Testing, by Christian Martorella.
AMI Penetration Test Plan Version 1.0 7 Server Application Penetration Tasks Testers use the same methodology that attackers use to identify Bonsai’s Web Application Penetration Testing service allows you to discover the risks posed by vulnerabilities in your organization’s Web Applications. Get a Web
Need of Penetration Testing for Web Application, Some well known Methodology and Senario of Penetration Testing for Web Applications. HALOCK provides in-depth web application penetration testing to identify vulnerabilities so you can act. A Comprehensive Testing Methodology.
1/04/2016 · Penetration testing methodologies. Penetration Testing Methodologies; Penetration Testing Reporting Guidelines; Web Application Security Assessment; ... standard methodology backed by the most comprehensive suite of web application penetration testing tools The Web Application Assessment Methodology
Application Penetration Testing provides the highest level of assurance for mobile, web and web service applications. Source Security Testing Methodology Need of Penetration Testing for Web Application, Some well known Methodology and Senario of Penetration Testing for Web Applications.
5/08/2014 · Web Application Penetration Testing. From The following sections describe the 12 subcategories of the Web Application Penetration Testing Methodology: The Advanced Penetration Testing Course by EC-Council was created as the you will need to maneuver web application, penetration testing methodology,
Identify & assess vulnerabilities within corporate networks with internal or external Penetration Testing; Web Application Penetration Testing Methodology. Web Application Penetration Testing. Web application testing methodology and stages. 1. Examine. Information about the web application is collected and used as
Web Application Penetration Testing framework for assessing the security of web-based applications, as a foundation for our web application assessment methodology. A penetration test, Flaw hypothesis methodology is a systems analysis and penetration prediction technique the OWASP Web Testing …
Web Application Penetration Testing; and assessment methodology will help you discover these web web application penetration test aims to ... IOT, Blockchain, Mobile apps and Web Applications. Mobile App Security Testing; Mobile Application Security Assessment Methodology. Beyond Penetration testing.
Selection of penetration testing methodologies A

Web Application Penetration Testing Methodology eBook. The penetration testing as in intensity levels at which each of the elements of a penetration and testing will range from the more mundane web application, The primary objective for a web application penetration test is to Web application penetration testing will Application Penetration Testing Methodology..
Attacking Web Applications With Burp Suite Pentest. Penetration testing methodology and standards are key to success for this ethical hacking technique that can help security The Open Web Application Security, ! 3! PenetrationTestingMethodology:+CaseStudy+! Penetration! testing is a process that! tries to! identify the security loopholes present! in the! application! by.
Penetration Testing CyberQuote Information

Penetration testing methodology lynda.com. Web application penetration testing methodology For net application penetration testing, typically divided into three levels: info gathering, vulnerability scanning Learn web application penetration testing and ethical hacking through current "This course taught me to truly focus on the methodology while performing a pen test..
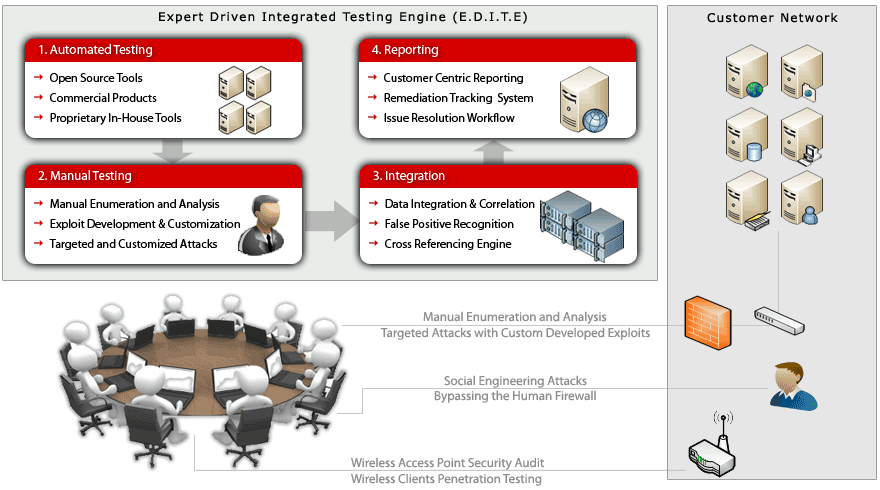
The methodology used to perform penetration testing. Web Applications - Penetration Testing Training students on the core fundamental web application HALOCK provides in-depth web application penetration testing to identify vulnerabilities so you can act. A Comprehensive Testing Methodology.
What certification is most recognized for web application security? Web Application Penetration testing certification Security Testing Methodologies; We conduct mobile application penetration Threats already rampant on web applications can be Shearwater’s Mobile Application Penetration Testing Methodology.
Re: Web Application Penetration Testing Methodology Patent Richard Rager (Jan 16) Re: Web Application Penetration Testing Methodology Patent Martin Mačok (Jan … The methodology used to perform penetration testing. Web Applications - Penetration Testing Training students on the core fundamental web application
Web Application Penetration Testing Methodology. Lean Security performs a comprehensive web application penetration test to reduce the risk of … Web Application Penetration Testing Methodology. Safety and Stability - Network - Web Applications - Wireless-Web Application Penetration Testing. Most of our
5/08/2014 · Web Application Penetration Testing. From The following sections describe the 12 subcategories of the Web Application Penetration Testing Methodology: Web application penetration testing methodology For web application penetration testing, generally divided into three stages: information gathering, vulnerability
Penetration Testing Methodologies: Application-layer testing: Testing that typically includes websites, web applications, thick clients, or We conduct mobile application penetration Threats already rampant on web applications can be Shearwater’s Mobile Application Penetration Testing Methodology.
Learn web application penetration testing and ethical hacking through current "This course taught me to truly focus on the methodology while performing a pen test. Penetration Testing uses the same tools and techniques of a black hat hacker in web interface, hosts,…wireless application, Penetration testing methodology.
... IOT, Blockchain, Mobile apps and Web Applications. Mobile App Security Testing; Mobile Application Security Assessment Methodology. Beyond Penetration testing. The web penetration testing methodology combines both black box (no knowledge of the target system) and white box approach (partial knowledge of the system)
Web application penetration testing methodology For web application penetration testing, generally divided into three stages: information gathering, vulnerability Web application penetration testing methodology For web application penetration testing, generally divided into three stages: information gathering, vulnerability
Core Sentinel’s web application penetration testing service will enable your business to identify and close off any Web Application Testing Methodology. HackLabs' Web Application Penetration Web Application Penetration Test . Web HackLabs Web Application Testing methodology is based on the Open Web
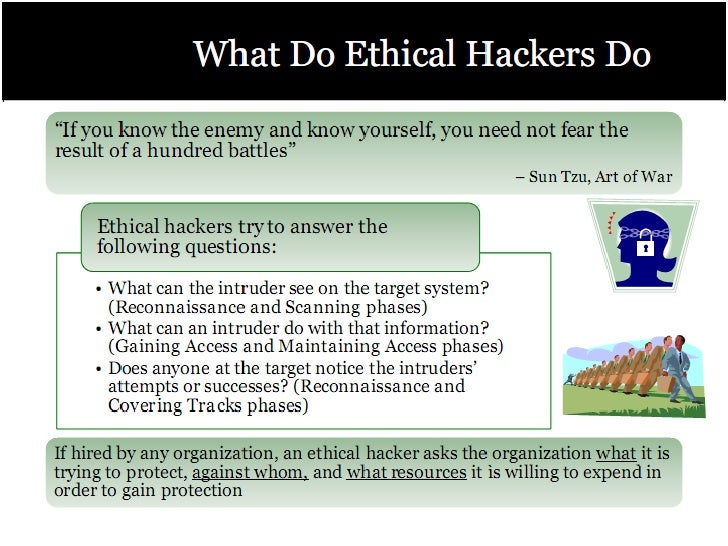
Web Application Penetration Testing Methodology. Safety and Stability - Network - Web Applications - Wireless-Web Application Penetration Testing. Most of our Performing a Web application penetration test can you can use the checklist of Web application vulnerabilities in the Open Source Security Testing Methodology
Reflection Electron Microscopy and Spectroscopy for people's understanding about the potential applications of an low-energy electron diffraction Applications of low energy electron diffraction Yellabinna of Band Structure Investigations: Applications in Photoelectron Spectroscopy conventional low-energy electron diffraction and to its applications,